|
||
 |
||
| A Newsletter for Unisys EAE and Agile Business Suite Clients | January 2020 | ||
Engineering Corner: Advanced Security Features in AB Suite 7.0By Howard Bell, Architect – EAE/AB Suite MCP Runtime and Debugger, Unisys
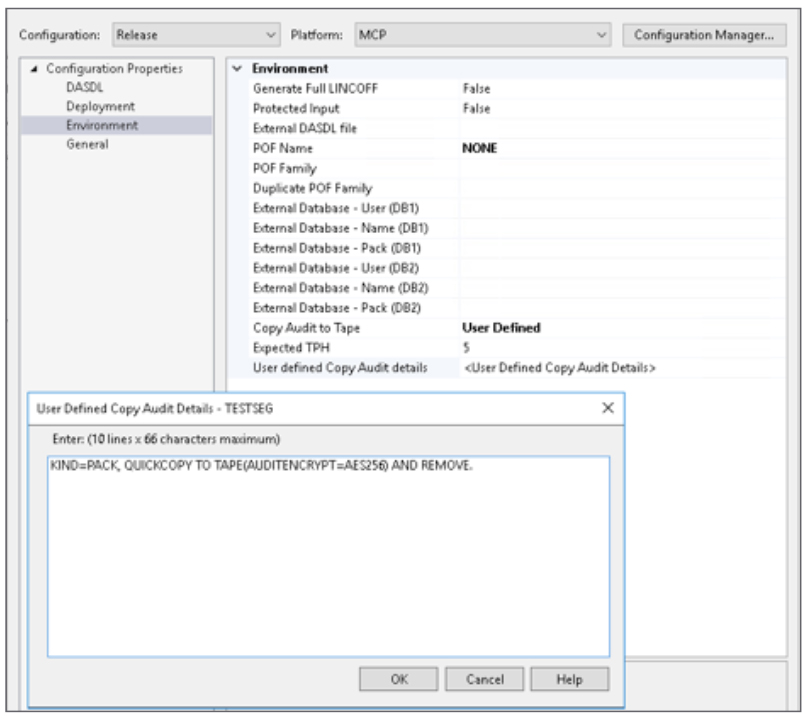
To that end, AB Suite 7.0 comes standard with the new, advanced security features described below. Together, they form the core of the most protected, most secure Secure RATLWith AB Suite 7.0 for ClearPath® MCP, you’re able to encrypt connections between your Client and Host RATL servers using the TLS 1.2 protocol, creating a secure data packet transfer for your transactions. To set up this feature, there are a few one-time MCP encryption steps you’ll need to execute. You’ll start by creating a Certificate Request via Security Center, processing the request through a certificate authority, creating a .P7B certificate file, and, finally, storing the certificate file in Security Center as a Trusted Key. This certificate must then be shared with the Client, so it can be imported into the respective Windows Trusted Store. To enable RATL TLS, you’ll need to update the Host *SYSTEM/CCF/PARAMS file to include the Secured Port and associated Service details. Naturally, you’ll need to restart the Custom Connect Facility (CCF) after updating its Params file. For additional detail about these steps, please refer to the Agile Business Suite Installation and Configuration Guide. To establish the Client connection, you’ll need to change the Host URL to indicate the TLS Service and TLS port. For example, you’ll need to use something along the lines of “x-ratltls:MCPHOST1:2449” instead of the standard “x-ratl:MCPHOST1:2448,” where “ratltls” and “ratl” correspond to the Service names defined in the Host *SYSTEM/CCF/PARAMS file. Complete these steps, and you’ll be able to use Secure RATL with the peace of mind that you’re protecting all in-transit data packets against unwanted viewing and interpretation. Secure DMSII AuditingIn AB Suite 7.0 for ClearPath MCP, you can prevent unauthorized access to your database update histories by encrypting the DMSII Audit Trail. By using the QUICKCOPY command in the “User defined Copy Audit Trail Details” configuration property, you can explicitly designate whether or not encryption occurs. When requesting encryption in a QUICKCOPY operation, you’re free to select TDES, AES256, or AESGCM algorithms. Just be sure to note that encryption is disabled by default. To enable this encryption, you’ll need to include “User Defined” in the “Copy Audit to Tape” property value, and then include the requisite syntax in the “User Defined CopyAudit Details” configuration property. For example: “KIND=PACK, QUICKCOPY TO TAPE(AUDITENCRYPT=AES256) AND REMOVE.”
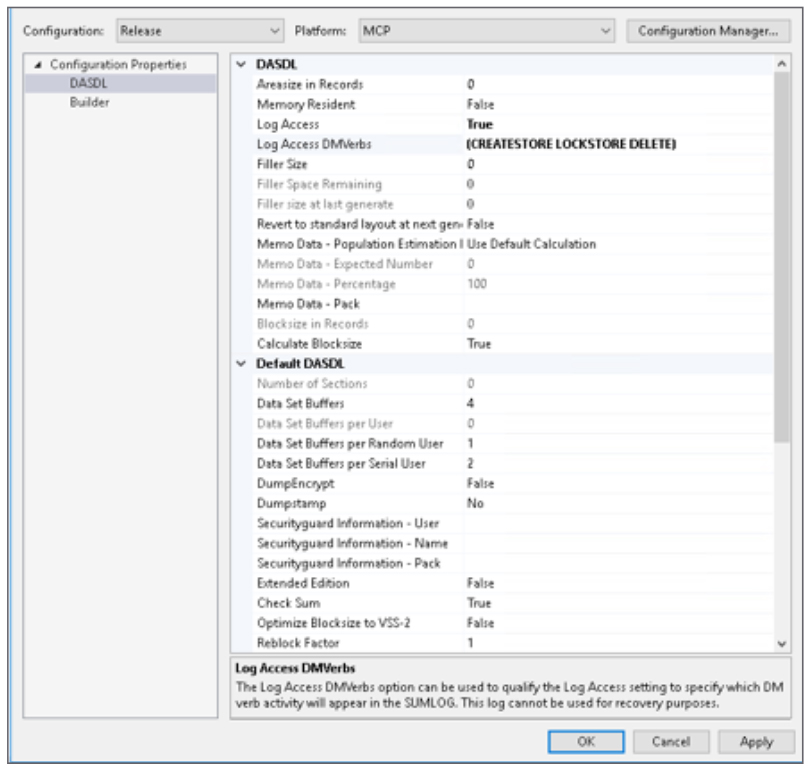
Additional information about this feature can be found in the Enterprise Database Server Data and Structure Definition Language (DASDL) Programming Reference Manual and Enterprise Database Server for ClearPath MCP Utilities and Operations Guide. Granular LoggingIn AB Suite 6.1, you could take advantage of a basic LOGACCESS capability that provided reporting – via the System Sumlog – for all DMSII operations against specific DMSII datasets. With AB Suite 7.0, we’ve refined the LOGACCESS feature by including support for the associated LOGACCESSDMVERBS feature. This allows you to specify which DM verbs will log information in the Sumlog for a specific structure. For example, you could specify just “LOCK,” “FIND,” “LOCKSTORE,” and “CREATESTORE.” The default value is “ALL.” A full list of DMVerbs is available in the Enterprise Database Server Data and Structure Definition Language (DASDL) Programming Reference Manual. For auditing purposes, it’s likely that only updates – adds, changes, or deletions – to data records in specific datasets need to be logged. You can do this by including “CREATESTORE,” “LOCKSTORE,” and “DELETE” in the “Log Access DMVerbs” Class configuration property. Note that the “Log Access” Class configuration property must be set to “TRUE.”
This provides a more clinical approach to logging specific DMSII operations against selected application DMSII datasets. |
||
|
||
| Subscribe | Unisys.com | Comment | Newsletter Archive | ||
|

 When building
When building