|
||
 |
||
| A Newsletter for Unisys EAE and Agile Business Suite Clients | April 2022 | ||
Single Sign-on and AB SuiteBy Gary Taylor, Senior Architect
In the simplest sense, this trust takes the form of a token that’s exchanged between users and the applications, services, etc. they wish to access. It’s validation, confirmed by the SSO solution, that these users are who they say they are and can access – and move freely between – any resources that accept that token.
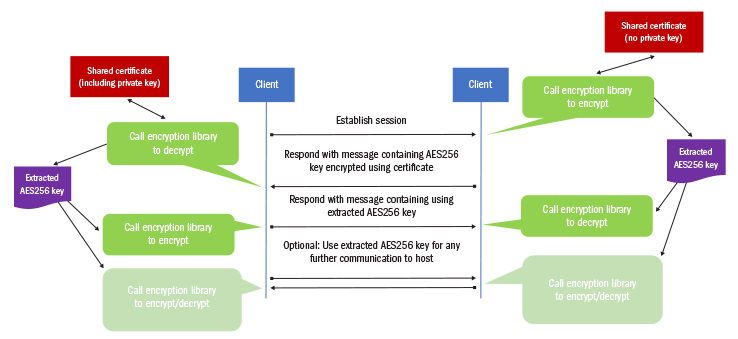
How it WorksThe first step was to create an external library that allowed us to encrypt and decrypt messages using the certificate’s public-private keys. These would then be called from the AB Suite application and ASP.Net code running on the web server. Because the Microsoft® Windows® and ClearPath® MCP environments can programmatically access certificates and encryption capabilities, we were able to develop two libraries, one written in .Net for use in Windows and another written in Algol for the MCP environment. Several factors proved key to making this approach work: we could use standard Client Tools capabilities, the message was passed via a standard field, and nothing special was required other than the external libraries. Also, the solution did not place any additional constraints on the client or host. Finally, it provided a framework to easily add a different type of trust, should one be required, The SSO solution utilizes the following logic flow:
Further, to eliminate the need to provide host-level credentials, a RATL VIEW with a predefined user was created for the ASP.Net sessions. This meant that at the application level, we’re unable to use GLB.USER. Rather, the LDL+ code populates a field that’s part of GLB.WORK, with the user ID in the message returned from the ASP.Net host. All existing references to GLB.USER were then updated to use this GLB.WORK field.
|
||
|
||
| Subscribe | Unisys.com | Comment | Newsletter Archive | ||
|

 Even as proprietary and commercial single sign-on (SSO) solutions flood the market, nearly all are built around a common theme: trust.
Even as proprietary and commercial single sign-on (SSO) solutions flood the market, nearly all are built around a common theme: trust.